Cybersecurity postures can be difficult to manage, especially for sprawling enterprise networks with a variety of platforms, software, data, and inputs under their umbrellas. Centralized sources for network and data management are crucial to security professionals who run the risk of missing important precursors to cyberattacks due to tool and data sprawl. Security Information and Event Management (SIEM) tools are one group of cyber solutions that work to collect and review data in a unified location so that security professionals can easily visualize and determine best next steps. Read on to learn about some of the top SIEM tools in today’s market:
Also read: Top Cloud Security Posture Management (CSPM) Tools 2021
Best Security Information and Event Management (SIEM) Solutions
What is a SIEM Tool?
SIEM, pronounced “sim,” stands for Security Information and Event Management. These types of tools are responsible for discovering and collecting data across network components, primarily in log and event data formats, and storing them in a central place on the platform. This singular source of data and network knowledge is intended to simplify the search and decision-making phases for network experts who look at systems vulnerabilities.
SIEM tools do not only collect and store data for security professionals to interpret, they also use threat intelligence, analytics, and alerting to automate network knowledge and fixes.
More on how SIEM works: Employing SIEM in the Network Security Fight
Features of SIEM Tools
SIEM tools offer a variety of features to help network security professionals manage threat detection, monitoring, compliance, and data visualization, among other core needs for diagnosing network security threats. Look for some of the following features in your search for the right SIEM tool for your business:
- EDR and/or XDR: Endpoint detection and response (EDR) and extended detection and response (XDR) are threat detection methods that simplify threat viewing.
- Intrusion Detection and Prevention System (IDPS): This type of software automates intrusion detection for networks.
- Automation: Many SIEM solutions automate threat detection and communication about security threats; specific examples include correlation, risk prioritization, Indicators of Compromise, and response.
- Analytics: Top SIEM tools typically offer a variety of templated or customizable analytics sets, often with workflow management features.
- System monitoring: Most SIEMs take a holistic approach to system monitoring, providing system metrics from network, database, application, email, IoT, vulnerability file integrity, data residency, cloud suites, virtualization sources.
- Dashboards and administrative tools: One of the core value-adds of SIEM tools is their consolidation of security information on dashboards; reporting and data visualization also make it possible to clearly share and review network security performance.
- Compliance features: Some SIEM tools emphasize regional and industrial regulatory compliance with specialized compliance packages and reports.
More analytics solutions to consider: Best Data Analytics Tools & Software
Best SIEM Tools
Rapid7 InsightIDR
Rapid7 InsightIDR is one of the top cloud SIEM solutions on the market and is particularly popular with users because of its several avenues for customer support. InsightIDR itself already offers a variety of security management features for endpoint, user, and penetration testing management, but can further increase its functionality when used in partnership with other Rapid7 Insight Platform products.
These other products that can be added as needed over time include: Threat Command for threat intelligence, InsightConnect for orchestration and automation, Services for expert managed and consulting services, InsightVM for vulnerability management, InsightAppSec for application security management, and InsightCloudSec for cloud security management.
Features:
- Advanced detections library with continuous activity baselining
- Metasploit penetration testing solution
- Endpoint Detection and Response (EDR)
- User and Entity Behavior Analytics (UEBA)
- Curated intrusion detection system (IDS) with access to additional network metadata
Pro: Detailed documentation, in-house agents, and an intuitive interface make this tool easy for users to self-start.
Con: InsightIDR only offers a cloud solution, while some users have expressed interest in on-premises and mobile access options.
Pricing: InsightIDR pricing starts at $5.61 per month per asset.
Splunk Enterprise Security
Splunk Enterprise Security is a cloud SIEM solution that emphasizes a varied portfolio of analytics and data visualizations for its users. The company is well-known for its deep portfolio of analytics solutions, which is why many users opt to use Enterprise Security in conjunction with other Splunk data and analytics management tools.
One of the most significant advantages that Splunk offers its users is a smart approach to risk-based alerting. Splunk alerting combines its own system knowledge to threat scoring and automated alerting, but it also gives users the hands-on capabilities to set up their own alert and detection thresholds. Some of the user customizations in this area include risk attribution to different users and network systems, alert mapping, and alert threshold setting.
Features:
- Data management across multicloud and on-premises deployments
- Event sequencing, alert management, risk scoring, and other customizations
- Risk-based alerting and alert queue management
- Threat detection in AWS, GCP, Azure, and other multicloud environments
- Splunk User Behavior Analytics feature
Pro: Risk tracking and alerting are adjustable for users, systems, and platforms monitored through the system.
Con: Some users do not feel this tool integrates well with third-party tools; they say it works best when used in conjunction with Splunk cloud and analytics solutions.
Pricing: Workload and Ingest pricing plans available. Contact the Splunk team for exact pricing information.
Securonix Next-Gen SIEM
Securonix Next-Gen SIEM is another analytics-driven SIEM solution that prides itself in fitting the varying security needs of a hybrid network. Not only does this solution focus on basic threat detection and data collection, but it uses smart rules, context, historical data, and automation to understand the risk of different network security incident scenarios.
Perhaps one of the most unique features of Securonix’s product is their content-as-a-service provided by Securonix Threat Labs. This means that the vendor’s research team researches different threat scenarios and indicators of compromise (IoC), and then they publish that data on Sigma and provide it as a part of their Next-Gen SIEM threat detection features.
Features:
- Analytics with machine learning, context enrichment, and user risk scoring
- Prebuilt analytics modules for common use cases
- Threat models that adhere to MITRE ATT&CK and US-CERT frameworks
- Fast search and long-term search available for historical data
- Over 350 connectors and API-based integrations for cloud visibility and threat detection
Pro: Real-time content-as-a-service production research for proactive threat detection is available through Securonix Threat Labs.
Con: Access control grouping is not intuitive to set up for different user permissions.
Pricing: Contact the Securonix marketing and sales teams directly for pricing information.
LogRhythm NextGen SIEM Platform

LogRhythm NextGen SIEM Platform is a preferred SIEM platform for users who want simple scalability in their security and threat management tools. The NextGen SIEM Platform is incredibly capsulated and can be broken down into core areas like RespondX, DetectX, and AnalytiX.
Some users have expressed that training is limited and difficult. However, LogRhythm closes some of this gap through the extensive as-a-service offerings provided by LogRhythm Labs. LogRhythm Labs is an internal LogRhythm team filled with experts to help users in the following security-adjacent areas: threat research and application; strategic integration, with industry-specific modules and ongoing plugin management; compliance research, mapping, and automation; and machine data intelligence (MDI) with a focus on third-party integration assistance.
Features:
- Threat monitoring, hunting, and investigation with incident response
- AnalytiX log management and centralization
- MDI fabric for data normalization and enrichment
- Threat scoring and risk-based prioritization (RBP)
- Consolidated Compliance Framework feature
Pro: LogRhythm offers a modular approach to SIEM, making it easy for organizations to add new modules and features as their security requirements grow.
Con: Training is limited and difficult, with some users struggling with areas like reports and alerts setup.
Pricing: Contact the LogRhythm marketing and sales teams directly for pricing information.
Exabeam Fusion SIEM
Exabeam Fusion SIEM is a growing top performer in the SIEM space that offers its customers many out-of-the-box, immediate functionalities to make it easier to deploy and scale over time. Although most tools in this market focus on threat detection at both a technical and user level, Exabeam boasts a higher detection rate when it comes to user anomalies, specifically citing their “market-leading behavior analytics” as a source for user threat detection data.
Fusion SIEM has the potential to be a strong contender for organizations in highly regulated industries and global regions. For example, HIPAA and SOX compliance packages assist with security and ethical data management in healthcare and publicly traded companies respectively.
Features:
- Machine learning and automation-driven behavior analytics
- Prescriptive, threat-centric use case packages
- Scalable central storage with rapid intelligent search available
- Turn-key TIR with prebuilt integrations for endpoint, cloud, and network security
- Automated Incident Diagnosis with behavioral analysis, threat diagnosis, use case classifications, and next-step checklists and response playbook
Pro: Exabeam offers some of the most extensive compliance features in the SIEM market, with compliance packages for PCI-DSS, HIPAA, SOX, and GDPR.
Con: Some users have commented on the limitations to third-party integrations, both by availability and ease-of-integration standards.
Pricing: Custom quotes are available from the Exabeam sales team.
RSA NetWitness Cloud SIEM
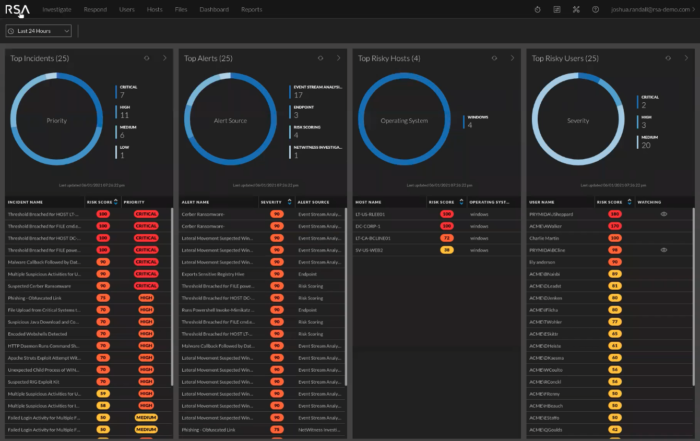
RSA NetWitness Cloud SIEM is another cloud SIEM that advertises itself as the choice for users who want simple licensing and initial setup. The company is also a leader in areas like integrated risk management, IT risk management, IT vendor risk management, and business continuity management; their focus on risk from all angles, especially with business continuity included, is a strong indicator that NetWitness can handle IT needs while still understanding and adhering to larger business goals.
NetWitness Cloud SIEM particularly shines in its in-depth knowledge of all kinds of data on a customer’s network. Their log and packet management goes beyond the basics, building up metadata knowledge to better contextualize network logs and potential security incidents.
Features:
- Data collection and analysis across logs, packets, endpoint, and IoT, as well as physical, virtual, and cloud platforms
- Throughput-based licensing model
- Fast search, reporting, and threat detection forensics
- Prebuilt compliance reports such as Basel II, Bill 198, FERPA, FFIEC, FISMA, GLBA, GPG13, HIPAA, ISO 27002, NERC CIP, NISPOM, PCI, SOX, and SSAE
- Log management and monitoring for public cloud and SaaS application sources
Pro: NetWitness offers advanced log and packet management features, such as log indexing and enrichment and sessionized metadata.
Con: NetWitness is fairly limited in its vulnerability protection features.
Pricing: Contact the RSA/NetWitness marketing and sales teams directly for pricing information.
IBM Security QRadar SIEM
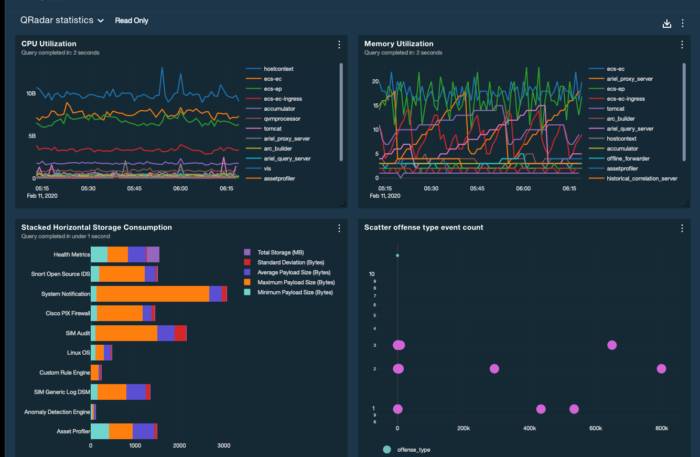
IBM Security QRadar SIEM is one of several top tools in IBM’s deep business technology portfolio, and it’s one of the strongest when it comes to incorporating a zero-trust strategy and best practices into a SIEM tool. This tool is frequently integrated with other IBM security solutions, and IBM Security XForce Threat Intelligence is automatically included for additional threat detection support.
One of the areas that customers like most in QRadar SIEM is the customizable queries portion. In this section, users can easily build, save, and filter through customized or templated queries, making it easier to reuse important search metrics after they’ve been used in the system. This solution comes in both on-premises and cloud formats, so businesses with different digital transformation goals and timelines can still find a way to fit QRadar SIEM into their cybersecurity arsenal.
Features:
- Continuous monitoring with a zero trust strategy
- Threat detection through network, endpoint, asset, user, risk, and threat data analysis
- Automatic parsing and normalization of logs
- Threat intelligence and support for STIX/TAXII
- Highly scalable, self-managing database
Pro: This tool integrates well with a variety of IBM portfolio tools, including IBM Watson.
Con: Pricing and licensing models are considered higher and more complex than some others in this market.
Pricing: Contact the IBM marketing and sales teams directly for pricing information.
McAfee ESM
McAfee Enterprise Security Manager (ESM) is a longtime favorite in the SIEM market, with straightforward applications and use cases for threat detection. As a legacy tool, McAfee ESM doesn’t necessarily receive as many updates as other tools in this market. But its simple setup and focus on user-friendly data visualizations make it a good option for businesses of all sizes.
Features:
- Content packs with templated security use cases
- Automated updates with near-zero downtime for users
- STIX-based threat intelligence feeds
- Flexible deployments across hardware and virtual machines
- Advanced analytics and rich context for threat detection
Pro: ESM is considered straightforward to deploy across cloud and server environments.
Con: Some users have expressed that new versions come out irregularly and with few improvements or add-ons to the system.
Pricing: Contact the McAfee marketing and sales teams directly for pricing information.
Also read: 12 Tips for Mitigating Security Risks in IoT, BYOD-driven Enterprises
Why is SIEM Important?
SIEM tools and best practices offer enterprises a variety of security and administrative benefits. Whether it decreases the chance of a breach, improves the daily work of network and security professionals, or increases data visibility for key stakeholders, consider investing in SIEM for some of the following benefits:
Simplified data logging
Collecting data logs can be tedious. But combing through logs later to find the exact historical data you need can be even more challenging. With flexibility for a variety of data types and a focus on constantly collecting data over time, network security logs will be stored in an up-to-date, easy-to-access fashion whenever your team needs to review them. SIEMs can log thousands of data bytes at a speed and accuracy that makes this tool a game-changer for efficiency.
Breach prevention
Security breaches are not only damaging to the data that has been compromised. They harm the users to whom the data belongs and the company’s reputation as well. There’s even the potential for legal and financial consequences from regulatory bodies. SIEM is one of the most important cybersecurity tools in preventing breaches because it organizes incoming data across all connected network components and makes it legible in a single pane of glass. With an easier visualization of network activity and potential problems, network security professionals can proactively monitor for and address security incidents before they turn into major breaches.
Learn more about the cost of a breach here.
Data and threat sorting
For organizations that collect thousands of data points that need to be monitored and reviewed for security issues, it can often be difficult to pinpoint those problems within the large data set. Even if you’ve found issues that need to be addressed, the vastness of a dataset can make it overwhelming to prioritize which threats need to be addressed first. With features like threat scoring and data filtering, SIEM tools automate the process of scoring threats and ranking their priorities for your team.
Staff and administrative efficiencies
Many of the manual sorting and analysis tasks that network and security staff used to do for security logs can now be handled by SIEM tools. Staff no longer have to spend valuable time on manual sorting work, and they also no longer need to rely on siloed tools for data knowledge.
Read the original article on Entreprise Working Planet here.
